An overview of a good InfoSec Strategy
Upgrade to paid to play voiceover
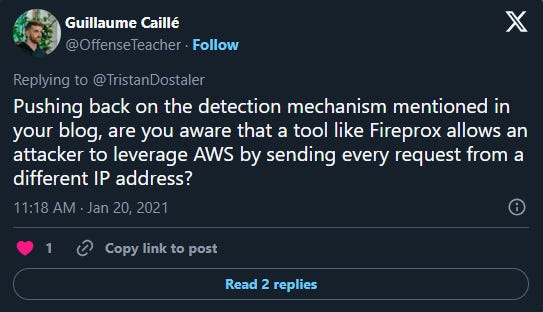
A friend of mine recently challenged my post SIEM 102 — Detect WordPress bruteforce where he proposed a tool that can effectively bruteforce WordPress from a lot of different IPs:
Source: https://twitter.com/OffenseTeacher/status/1351927187180572673
Some background
Some background are required to understand his response.
First, it is important to know that …
Keep reading with a 7-day free trial
Subscribe to Tristan’s Cybersecurity Substack to keep reading this post and get 7 days of free access to the full post archives.