In this post I’ll explain the CIS controls and how they can be used to start securing an enterprise.
When you’re in a medium or big environment and the maturity level of the InfoSec is around zer0, it’s hard to decide where to start in securing your environment. Do we need to update the systems, software and hardware first? Do we need to focus on awareness with the employees? The list is long; it can seem like there is no possible way to reduce the global risk.
Funny note: since I started writing this post, the controls got an update both in the number (previously 20, now 18) and in how they are organized! You can find an overview of what changed here: https://www.sans.org/blog/cis-controls-v8/
Context
There are multiple framework that can be used to help decide what to do and in what order. The first that comes to mind is the NIST Cybersecurity Framework. If you’re already an expert in InfoSec, you probably know about this framework and understand how it’s an excellent framework. But as an expert or as a newly appointed CISO, this framework is not ideal when you’re starting from near zer0. That’s because it’s complete, too complete; and complex. There is no prioritization and it addresses all that needs to be addressed at some point. That’s why the 18 CIS controls are ideal to start.
These 18 controls are ordered by logical priority. For example, there is no need to choose the best Antivirus if your systems are not updated. But you can’t update your systems if you don’t know what needs to be updated, hence why an inventory is crucial.
The 18 CIS Controls
You can find the controls here: https://www.cisecurity.org/controls/cis-controls-list/
You can also download a PDF or Excel version here:
Latest version: https://learn.cisecurity.org/control-download
V7.1: https://learn.cisecurity.org/control-download-v7.1
Here you can find a detailed explanation of all the controls: https://controls-assessment-specification.readthedocs.io/en/stable/
The controls were grouped in a logical manner in the V7, but this grouping has been removed in the V8. For an easier reading of my post, I’ll keep the original grouping and reorganize based on the mapping changes, however, this shouldn’t be understood as a categorization of what you should do. To categorize, they developed “Implementation Groups” designed to help organization of different size focus on the right safeguards. Here are the original groups: basic controls, foundational controls and organizational controls.
Here is why they changed the way they organized the controls:
Historically, the CIS Controls were ordered in sequence to focus an enterprise’s
CIS_Controls_v8_Guide.pdf
cybersecurity activities, with a subset of the first six CIS Controls referred to as
“cyber hygiene.” However, this proved to be too simplistic. Enterprises, especially
small ones, could struggle with some of the early Safeguards and never get around
to implementing later CIS Controls (for example, having a backup strategy to help
recover from ransomware). As a result, starting with Version 7.1, we created CIS
Controls Implementation Groups (IGs) as our recommended new guidance to prioritize
implementation.
Basic Controls
Here is a brief explanation of each basic controls:
- Inventory and Control of Enterprise Assets
- It’s important to always have an up to date list of all the hardware in our possession. That includes the servers, workstations, switches, etc. In our cloud world, I would include all the virtual hardware in the cloud also, like load balancers, VMs, SaaS, FaaS, etc.
Once you have this list in your possession, it’s simply a matter of prioritization. You can make sure no rogue devices are allowed in your environment. They can be updated as needed. You can remove unneeded devices, etc.
Another great advantage of this list is when you are responding to an incident: it will allow you to better understand what happened, where and how. Once the incident is resolved, you’ll know what to restore from previously well designed backup plans.
There are many other advantages to lists like this, I’ll let your imagination run free!
- It’s important to always have an up to date list of all the hardware in our possession. That includes the servers, workstations, switches, etc. In our cloud world, I would include all the virtual hardware in the cloud also, like load balancers, VMs, SaaS, FaaS, etc.
- Inventory and Control of Software Assets
- Like the hardware assets, it’s important to know and track all the software used in our environment. That will allow us to continuously validate for outdated software or if some of them have known vulnerabilities. We can also use this inventory to detect suspicious behavior. For example, if a tool like PsExec is installed on a HR computer. Another use would be to detect unlicensed software or software licensed with bad licenses that could be a threat to the enterprise (like a license requiring you to opensource all the tools developed with it’s software, like the Elastic License or the GNU GPL license).
- Data Protection
- The wording “Data Protection” is voluntarily broad. The official definition of this control is “Develop processes and technical controls to identify, classify, securely handle, retain, and dispose of data“. As you can see, it means nothing and everything at the same time. The idea of this control is that a systematic process should be put in place around data manipulation. We need to analyze how data should be handled when a new data set is added to a software we use of develop, or a new software is adopted. Most company will first acquire new data without thinking too much about it. For example, who asked if and how should Google Analytics be implemented before it was done? But there is an inherent responsibility to all this data handling. This responsibility should be taken seriously and the data should be:
- Identified, meaning it should be crystal clear what the data will be;
- Classified, meaning some tags should be added to this data like the type of data and the sensitivity for customers and for the internal business;
- Securely handled, meaning the process around the data should be clear: encryption at rest, encryption in transit, who has access, is it sanitized, etc.;
- Retained, meaning the process on how long the data should be kept and what triggers the need for it’s destruction should be clear;
- Disposed, meaning the process for disposing securely of the data should be clear;
- The wording “Data Protection” is voluntarily broad. The official definition of this control is “Develop processes and technical controls to identify, classify, securely handle, retain, and dispose of data“. As you can see, it means nothing and everything at the same time. The idea of this control is that a systematic process should be put in place around data manipulation. We need to analyze how data should be handled when a new data set is added to a software we use of develop, or a new software is adopted. Most company will first acquire new data without thinking too much about it. For example, who asked if and how should Google Analytics be implemented before it was done? But there is an inherent responsibility to all this data handling. This responsibility should be taken seriously and the data should be:
- Secure Configuration of Enterprise Assets and Software
- When you use a software, most of the time it’s not secure by default but can, and should, be hardened. Of course, this is a never ending process and every time a software received a major upgrade, the process should be revisited. This point should be applied to everything and anything that can be configured; mail server, FTP server, Windows, Linux, Android, iOS, a switch, etc. And the possibility to securely configure a software should be in it’s selection criteria when deciding which software to use to fill a need.
- Account Management
- There should be a well defined account management process and architecture. For example, if you are using Windows, you should follow the 3-tier architecture, or it’s newer version, for the administrators account: https://docs.microsoft.com/en-us/security/compass/privileged-access-access-model. You should also make use of LAPS for local administrators (as opposed to having always the same user with the same password for all computers in the company). Accounts for services should have a strong password managed in a password vault, each service having it’s own account with it’s own password and permissions.
- Access Control Management
- “Access Control Management” applies to both physical and technological accesses. It is important to have a clear and well defined process to manage access to users and service accounts, grant them privileges or revoke access. We need to be able to easily grant or remove all access to systems and enterprise assets to users, whether they are new or not an employee anymore. The worst case scenario is forgetting to remove some or all accesses to an employee with bad intentions. But there is also a lost in productivity and/or security risks if it’s hard to grant accesses with the least privileges possible.
- Continuous Vulnerability Management
- As we are all too aware, new vulnerabilities are found weekly, probably event daily. After they are found, it is a matter of time before they are exploited. Because there is a continuous flow of vulnerability, it is important to evaluate the risks, track and prioritize them. Of course, this point is directly dependent of the first 2 CIS Controls.
- Audit Log Management
- When an incident is detected, it is often too late to start adding tools that could help understand how the attack occurred. It is not rare to see that the logs have simply been deleted by the attacker. Because of this, it is important to continuously collect the logs in a centralized location, like a SIEM (see my posts on the subject: https://www.tristandostaler.com/category/information-technology/infosec/siem/). Once we collect all these logs, we can start to detect attacks as they occur and stop the attacker in it’s track, instead of waiting for a true incident to occur. These logs can also be useful to understand how an attack happened and what can be done so it doesn’t happen again.
Foundational Controls
Here is a brief explanation of each foundational controls:
- Email Web Browser and Protections
- Probably the most prevalent initial access tactic, phishing, through email or other means, can have a devastating impact if successful. This is why it is important to have protections in place to detect and block these attacks. There are many layers that can be implemented to protect us. We can start from the human aspect by providing training to detect phishing and other forms of attacks. We can also have an email filter, use DNS servers like Quad9, a modern browser that can detect typical attacks, an antivirus (or it’s new form: an EDR), etc.
- Malware Defenses
- This 2 words category is one of the most complex technically speaking. The idea of this category is to put in place defenses against malware. One of the first layer to do this is to use an antivirus (or it’s new form: an EDR), but it is nowhere near sufficient. New EDRs are really hard to bypass, and get harder by the day, but they are far from perfect. This is why it is important to have other defenses in place. But configuring these defenses so they detect enough, but not too much, potentially malicious activity is hard. For example, if you want to restrict what executables can run on your computers, you need to know what are the complete list of executables and understand that there will be a lot of demands to ask for new software to be added to the exception list. And what do you do with developers?
This category is difficult but really important and the strategy should be revised at least yearly.
- This 2 words category is one of the most complex technically speaking. The idea of this category is to put in place defenses against malware. One of the first layer to do this is to use an antivirus (or it’s new form: an EDR), but it is nowhere near sufficient. New EDRs are really hard to bypass, and get harder by the day, but they are far from perfect. This is why it is important to have other defenses in place. But configuring these defenses so they detect enough, but not too much, potentially malicious activity is hard. For example, if you want to restrict what executables can run on your computers, you need to know what are the complete list of executables and understand that there will be a lot of demands to ask for new software to be added to the exception list. And what do you do with developers?
- Data Recovery
- When an incident occurs, be it a ransomware, a deleted database table in production because of a bad manipulation or any other cause, it is important to be able to recover the lost data in a timely manner. There are multiple strategies for this, and it is not rare to see multiple strategies being used at the same time for deadly crucial data. A “3-2-1 backup” strategy* of important folders is an example. Or an “Active/Active” architecture, combined with a constant (ex: every hour) duplication of the data to a cloud storage solution is another example where multiple strategies are combined.
* I found this nice article talking about different backup strategies. If backup strategies is something useful for you, I think you’ll find it interesting.
- When an incident occurs, be it a ransomware, a deleted database table in production because of a bad manipulation or any other cause, it is important to be able to recover the lost data in a timely manner. There are multiple strategies for this, and it is not rare to see multiple strategies being used at the same time for deadly crucial data. A “3-2-1 backup” strategy* of important folders is an example. Or an “Active/Active” architecture, combined with a constant (ex: every hour) duplication of the data to a cloud storage solution is another example where multiple strategies are combined.
- Network Infrastructure Management
- It’s important to keep a list of all the enterprise assets. But it’s equally important to make sure the network they are connected to is secure. This is done, partly, by continuously tracking (and/or scanning) the devices in the network and then making sure they are correctly configured. It happens really often to induce a vulnerability in the network by installing a new device without changing the default vulnerable configurations. These devices can be switches, firewalls, wireless access points, etc.
- Network Monitoring and Defense
- While it’s important to continuously maintain the network devices, nothing is perfect. This is why it’s important to “Operate processes and tooling to establish and maintain comprehensive network monitoring and defense against security threats across the enterprise’s network infrastructure and user base”. To get more information on this, see my series on SIEMs: https://www.tristandostaler.com/category/information-technology/infosec/siem/
Organizational Controls
Here is a brief explanation of each organizational controls:
- Security Awareness and Skills Training
- Once you cover the basics, the most probable way in the network is through human. Bad actors will use techniques like Phishing to get a foothold for further attacks. This is why it’s important to have a security awareness program. With this, you can raise the level of your employees awareness so they better recognize these type of attacks. This can reduce the risk to the enterprise. Once you have an awareness program, it’s important and useful to keep statistics on the results so the recidivists can be better trained.
- Service Provider Management
- You probably of the famous Supply Chain Attack, an old concept that got popularized in 2020 because of the SolarWinds attack. To reduce the risk of getting caught off-guard by these types of attacks, it’s important to evaluate service providers and ensure these providers have proper processes to protect our data.
- Application Software Security
- If your enterprise develops software of some kind, it’s important to have a process to prevent, detect and remediate issues in these software. Many tools and techniques can be used for this, from code review with a security point of view to having a SAST, DAST, IAST or RASP. If you don’t have security specialist that can do code review, multiple security firms can help you with this.
- Incident Response Management
- Even if you do everything described in this post, hackers can still get through. This is why it is important to plan before it happens and have a well defined Incident Response process.
- What would you do if an incident happened?
- Who would you call for help?
- Who would be implicated and/or informed?
- Who is responsible to handle the technical aspects of the incident response?
- What and where are the response playbooks?
- Etc.
- Even if you do everything described in this post, hackers can still get through. This is why it is important to plan before it happens and have a well defined Incident Response process.
- Penetration Testing
- It is always recommended to periodically do a Penetration Test (en français on dit “Test d’intrusion” 😉 ). I have some clients that do them yearly and other monthly or even weekly (targeting different things (internal, websites, external, etc.)). It is important to regularly do this because security is hard and it’s really easy to miss something, even when we do everything right.
My opinion on these controls
Although the order I explain these controls make sense somewhat, these controls shouldn’t be addressed purely in order, but rather in parallel by carefully analyzing our current stance and addressing the point with the bigger gaps first.
As I explained, there are other, more complete framework to work with. But I personally think the CIS controls are an excellent starting point as well as a cheat sheet to keep handy. In this post I mentioned the controls at a high level, but you’ll find that the complete version has a lot more details.
I often work on Incident Responses for clients where they ask me for some resources to help them make sure they can work to secure their environment. I always recommend the CIS Controls because they are useful for technical people and understandable by the management.
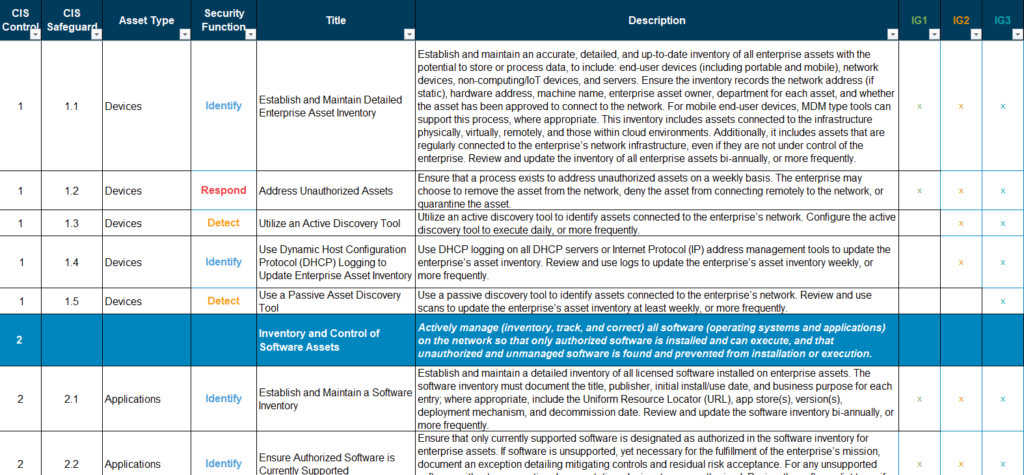
The Excel version is especially useful to organize and prioritize the controls as we work on them. Here’s a picture of how it looks:
Feel free to leave your comment down here for any questions or comments.
