I have posted a few articles about SIEMs and I have all done them using Logz.io for my examples. I recently switched to Humio and transferred all the logs and automations I have. In this post I explain why I did this transfer.
Here are the posts I did using Logz.io for my examples:
- https://www.tristandostaler.com/siem-101-introduction/
- https://www.tristandostaler.com/siem-101-initial-setup/
- https://www.tristandostaler.com/siem-101-basic-usage/
- https://www.tristandostaler.com/siem-102-detect-windows-bruteforce/
- https://www.tristandostaler.com/siem-102-detect-wordpress-bruteforce/
- https://www.tristandostaler.com/siem-201-what-is-sysmon/
- https://www.tristandostaler.com/siem-202-detecting-remote-psexec/
The Reasons
There are 3 reasons why I switched:
- The retention period for the free tier
- The ease of use of the platform
- It’s powerful features for advanced users
The Retention Period For The Free Tier
In Logz.io, the free version allows for 1 GB of log sent per day, and the logs are kept for 1 day. However, I have been using Logz.io for a long time so my account is using their previous free version which allowed for 3GB of log per day, for 3 days retentions.
Source: https://logz.io/pricing/
However, Humio, with their community version, allows to send up to 16GB of log per day, with a retention period of 7 days.
Source: https://www.humio.com/getting-started/community-edition/
Since I am using these platforms to test different strategies of using SIEMs, I need more than 3 GB per day, and ideally I need more than 3 days of retention, because sometimes I debug something a few days after a bug is detected (I have a fulltime job after all). So by having a lot more data I can send, and having this data retained for a longer period, Humio better fits my needs.
I do need more than 3 GB per days because I am sending logs from multiple machine, Windows, Linux and other devices like my router. Also, I am testing tools like the new Sysmon for Linux and to fully test it, I need to be able to send a lot of data by having a non-optimized configuration so that I can understand how to optimize the config. Another tool I am testing is Packbeat which send information about every connection made to a machine (there are configuration that can be done to reduce the noise).
The Ease Of Use Of The Platform
Humio is really easy to use. For basic use, it’s as easy as Logz.io. However, for some features like modifying how the data is parsed, in Logz.io it is a lot harder than in Humio. In Humio, customizing how the data is transformed before being saved in the database is a lot easier: you simply query for the data you want to transform (“*” for everything, I query by type so “type = syslog”) and then you can use powerful functions to modify the data. When you are satisfied, save the query and use it in the parser configuration.
Here is an overview of my config for Syslog:
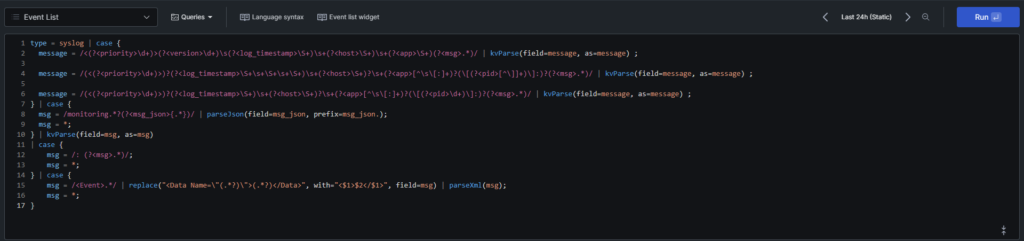
It is important to note however that it took me some time to find the optimal way to configure the parsers. That would need a blog post of it’s own, but in a few words, the easiest way is to use saved queries as much as possible because it’s easier to modify. I only have 2 parsers, one for winlogbeat and one for filebeat. Filebeat is the most complex as it handles different types, but both of them use the saved query “Post Process”. This saved query itself uses 2 other saved queries: “Normalize” and “Enrich”. This way, I can modify the “Normalize” query, save it, and all my logs now have the new config.
The Powerful Features For Advanced Users
It is, in my opinion, extremely important that a SIEM is easy to use for beginners. Unless your in a multi-billion enterprise, I don’t think it should be required to hire an expert with 10 years experience in your specific SIEM technology to be able to use a SIEM and secure your enterprise.
But as much as I hold on tight to that principle, I think a SIEM should also allows for advanced users a way to be more efficient; an “expert mode”. For me, it’s OK if that expert mode is by using an API to update a config or an alert, but in Humio, we have the advantage to have this expert mode easily available and usable. The downside is that Humio is a little bit harder to use that Logz.io (or Kibana based SIEMs), so it’s definitely not a perfect solution. But I think they found an acceptable balance between ease of use and power user features for most companies.
Some of these features for Humio are:
- The way we can modify parsing queries using already ingested logs to test against real data
- The way we can create alerts (it’s almost the same as a saved query)
- The way they designed alert throttling is really powerful
- They support multiple type of actions for alerts (email, HTTP requests, etc.) and the configuration is easy to do
- The query language support “Piped” queries
- The documentation is complete and well done
- It is relatively easy to segregate data and control who has access to what with which rights
- Etc.
Conclusion
Although Humio is not a perfect solution and is missing some key SIEM features that some enterprise would look for, in my context it is more than enough and I am definitely using it as a SIEM.
The fact that we can send a lot of data also allows us to test the platform and other technologies. And the “expert mode” is definitely enjoyable to use, a lot more than many other platforms I have tried.
Feel free to leave your comment down here for any questions or comments.
